Analysis - Brute force attack log analysis
Recently my server experienced heavy brute force attack, on an average two requests per second. Attacker was trying to get SSH access to the server. But still, everything stayed intact. It was like a night-mare when I realized it.
In this article, I’m presenting basic analysis of the log files. Especially, top IPs, ports and usernames used in the attack.
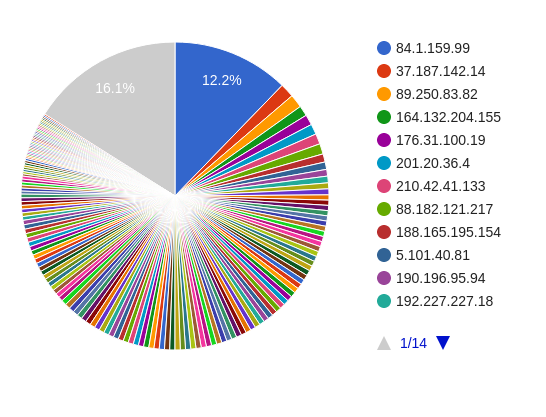
IP addresses
Total 363 IPs are used in the attack almost from every country. Every IP is used at-least twice in the attack. Highest number of times a single IP used in attack is 314 times.
Following are the top 5 IPs used in the attack
| # | IP | Count |
|---|---|---|
| 1 | 84.1.159.99 | 314 |
| 2 | 37.187.142.14 | 38 |
| 3 | 89.250.83.82 | 36 |
| 4 | 164.132.204.155 | 28 |
| 5 | 176.31.100.19 | 28 |
Following is the pie chart representing the percentage usage of IP addresses in the attack.
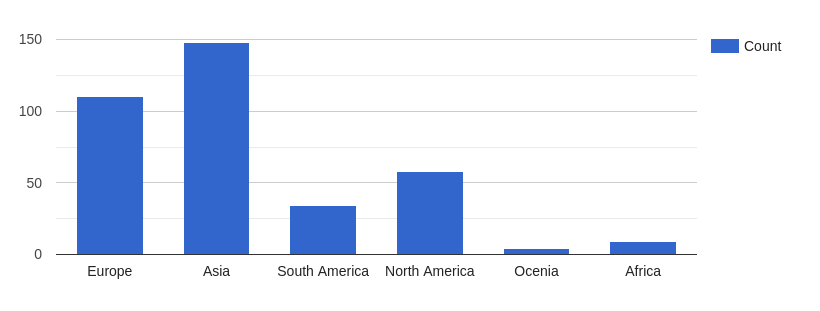
Continent-wise IP address data
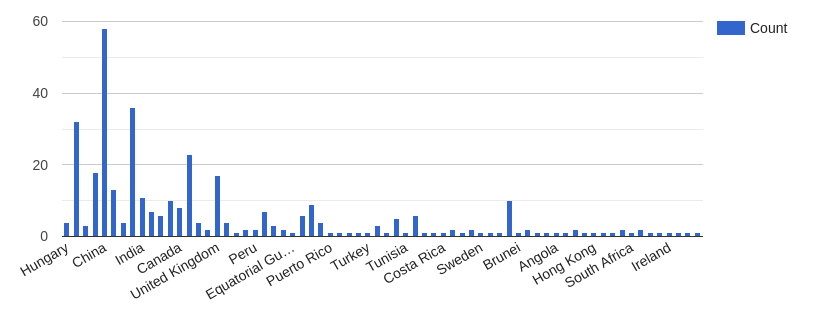
Following are the top 5 country IP addresses used in the attack
| # | Country | Count |
|---|---|---|
| 1 | China | 58 |
| 2 | United States | 36 |
| 3 | France | 32 |
| 4 | Republic of Korea | 23 |
| 5 | Brazil | 18 |
Country-wise IP address data
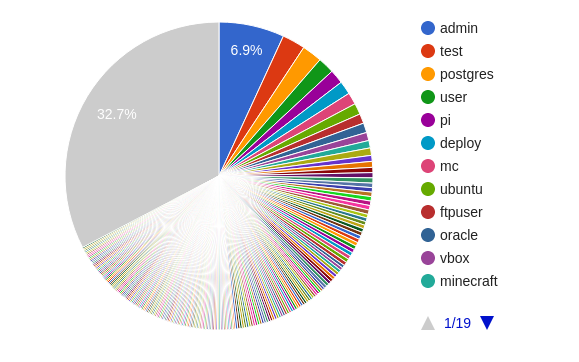
Usernames
Attacker used a total 635 usernames to brute-force the server. Attacker used usernames stating with admin to minecraft and also 0. It seems weird when someone uses only digits in username. Its funny to use usernames made of only single digit.
Following are the top 5 usernames used in the attack
| # | Country | Count |
|---|---|---|
| 1 | admin | 176 |
| 2 | test | 62 |
| 3 | postgres | 54 |
| 4 | user | 44 |
| 5 | pi | 38 |
All usernames used in the attack
Ports
A total of 1238 ports are used in the attack. Starting with port number 1088 to 65460. Each port is used atleast for two times in the attack
Following are the top 5 ports used
| # | Port number | Count |
|---|---|---|
| 1 | 47072 | 12 |
| 2 | 9224 | 6 |
| 3 | 1664 | 6 |
| 4 | 58104 | 4 |
| 5 | 51018 | 4 |
Advice
-
Never ever use password based authentication for SSH access.
-
Implement a security system to block IPs or hosts trying to get into the system like fail2ban.
-
Never use common usernames during user account creation. Better to use cryptic usernames like passwords.
-
Regularly analyze system logs and take necessary actions.
-
Close all unused ports. Expose only required ports to public internet with appropriate security measures in place.
-
Setup alert system to get notified if something unusual happens in the server like a user logged in to the service, a critical service stopped, a new service started, change in the filesystem etc.
-
Lastly, share required data with the community to help others.